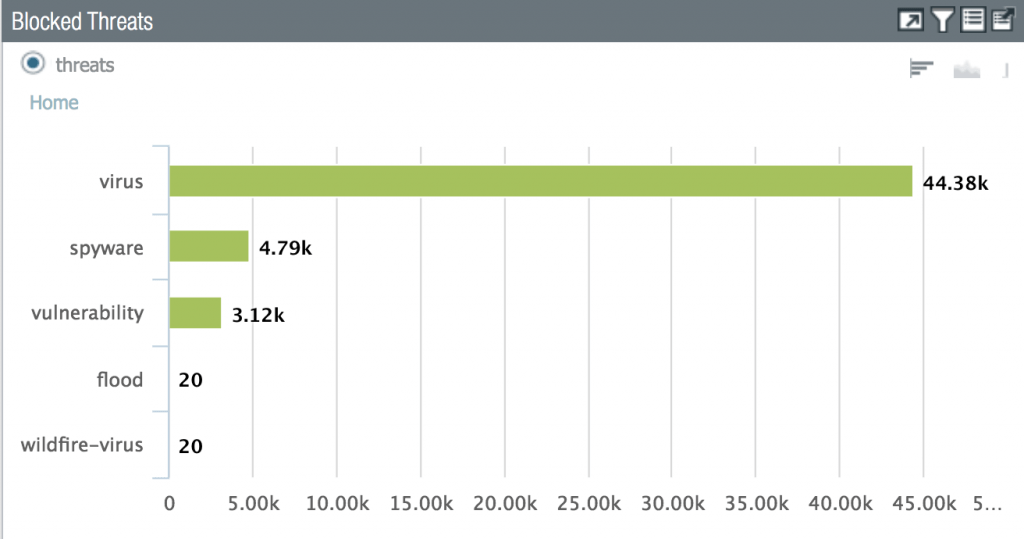
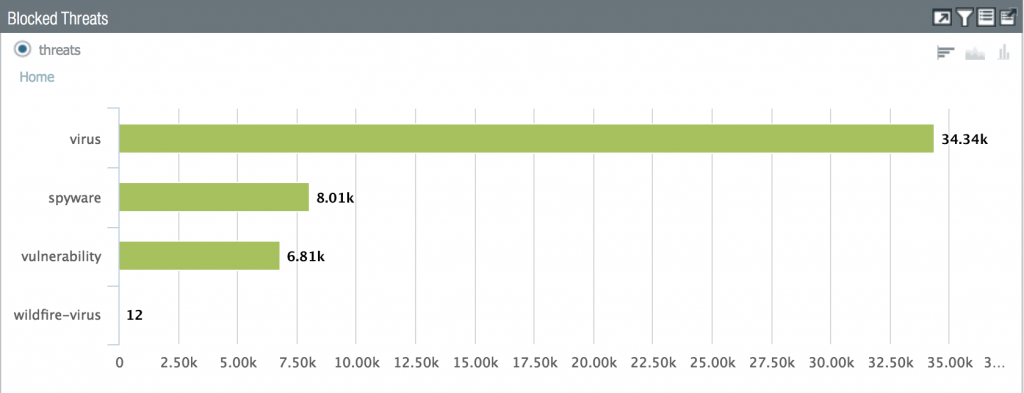
With the addition of AppID functionality to fw.noc’s beta branch, we can now declare Phase 2 of the firewall migration project complete! AppID is a huge step for us as this is feature is not offered by any other vendor at this time. This will allow us to create new firewall rules based on Application signatures, rather than on a port and protocol. Here are a couple of screenshots from fw.noc that show the difference, from our admin view, between the two.
The first screenshot is a sample of our current firewall rules that we put in front of network equipment. One group is TCP ports, the other is UDP. We can mouse over a group to get a list of ports contained in that group:

This next screenshot shows the rules for the same IP address after converting them to AppID. Rather than a port and protocol, we have applications: ssh, web-browsing (http), ssl (https), and snmp:

The rule is pushed from fw.noc onto the relevant Palo Alto virtual firewall, and the result is this (apologies for formatting):

These new rules still have a port and protocol setting. By default we are using ‘application default’ which will still only allow this application on its standard port. Now, rather than allowing any traffic on port 22/tcp as we were with port/protocol rules, we are only allowing ssh traffic on port 22/tcp with AppID rules. We have the ability to create a rule that allows an App on an alternate port, or any port. For example, we can create a rule that allows ssh on port 2022/tcp, or a rule that allows ssh on any tcp port.
We have two steps going forward with this feature. The first will be add AppID to fw.noc self service. The next will be to migrate as many of our existing rules to AppID where possible.
We are working on our goals for Phase 3 of this project, which we hope to announce very soon.